2020-04-11
How To Know If An E-Mail Is Trustworthy

Louis Columbus
2020-04-11
How To Know If An E-Mail Is Trustworthy
Source: Forbes Business Council





Bottom Line: Phishing is the leading cause of all breaches, succeeding because impersonation, redirection, and social engineering methods are always improving. And, phishing is only one way emails are used in fraud. Businesses need to understand if an email address can be trusted before moving forward with a transaction.
Microsoft thwarts billions of phishing attempts a year on Office365 alone by relying on heuristics, detonation, and machine learning, strengthened by Microsoft Threat Protection Services. In 2018 Microsoft blocked 5 billion phish emails in Office 365 and detonated 11 billion unique items by ATP sandboxing. Microsoft is succeeding with its cybersecurity partners in defeating phishing attacks. Phishers are going to extraordinary lengths to discover new techniques to evade detection and successfully carry out phishing attempts. By analyzing Office 365 ATP signals, Microsoft sees phishers attempt to abuse many legitimate cloud services, including Amazon, Google, Microsoft Office365, Microsoft Azure, and others. Microsoft is creating processes that identify and destroy phishing attempts without impacting legitimate applications’ performance.
Phishers’ Favorite Trojan Horse Is Office365 Followed By Cybersecurity Companies
Phishers are hiding malicious links, scripts and, in some cases, mutated software code behind legitimate Microsoft files and code to evade detection. Using legitimate code and links as a Trojan Horse to successfully launch a phishing campaign became very popular in 2019 and continues today. Cybercriminals and state-sponsored hackers have been mutating legitimate code and applications for years attempting to exfiltrate priceless data from enterprises and governments globally. Office365 is the phisher’s Trojan Horse of choice, closely followed dozens of cybersecurity companies that have seen hackers attempt to impersonate their products. Cybersecurity companies targeted include Citrix, Comodo, Imperva, Kaspersky, LastPass, Microsoft, BitDefender, CyberRoam, and others.
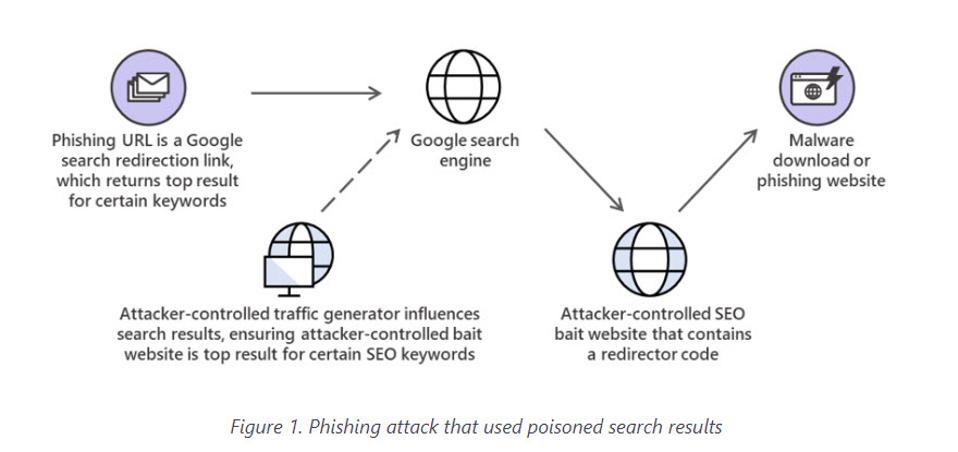
Using Trojan Horses To Hijack Search Results
In 2019 Microsoft discovered a sophisticated phishing attack that combined impersonation, redirection, and social
engineering methods. The phishing attack relied on using links to Google search results as a Trojan Horse to deliver URLs
that were poisoned so that they pointed to an attacker-controlled page, which eventually redirected to the phishing page.
Microsoft discovered that a traffic generator ensured that the redirector page was the top result for specific keywords.
The following graphic explains how the phishing attack was used to poison search results:
HTTPS://WWW.MICROSOFT.COM/SECURITY/BLOG/2019/12/11/THE-QUIET-EVOLUTION-OF-PHISHING/
Using this workflow, phishers attempted to send phishing emails that relied on legitimate URLs as their Trojan Horses from legitimate domains to take advantage of the recipient’s trust. Knowing which e-mails to trust or not is becoming foundational to stopping fraud and phishing attacks.
How Kount Is Battling Sophisticated Attacks
Meanwhile, email addresses can be a valuable source of information for businesses looking to prevent digital fraud. Misplaced trust can lead to chargebacks, manual reviews, and other undesirable outcomes. But, Kount’s Real-Time Identity Trust Network calculates Identity Trust Levels in milliseconds, reducing friction, blocking fraud, and delivering improved user experiences. Kount discovered that e-mail age is one of the most reliable identity trust signals there are for identifying and stopping automated fraudulent activity.
Based on their research and product development, Kount announced Email First Seen capabilities as part of its AI-powered Identity Trust Global Network. Email First Seen applies throughout the customer journey, from payments to account login to account creation. The Identity Trust Global Network consists of fraud and trust signals from over half a billion email addresses. It also spans 32 billion annual interactions and 17.5 billion devices across 75 business sectors and 50-plus payment providers and card networks. The network is linked by Kount’s next-generation artificial intelligence (AI) and works to establish real-time trust for each identity behind a payment transaction, log in or account creation
Email Age Is Proving To Be A Reliable Indicator Of Trust
A favorite tactic of cybercriminals is to create as many new e-mail aliases as they need to deceive online businesses and defraud them of merchandise and payments. Kount is finding that when businesses can identify the age of an e-mail address, they can more accurately determine identity trust. Kount’s expertise is in fraud prevention effectiveness, relying on a combination of fraud and risk signals to generate a complete picture of authentication details. The following graphic illustrates what a Kount customer using Email First Seen will see in every e-mail they receive.
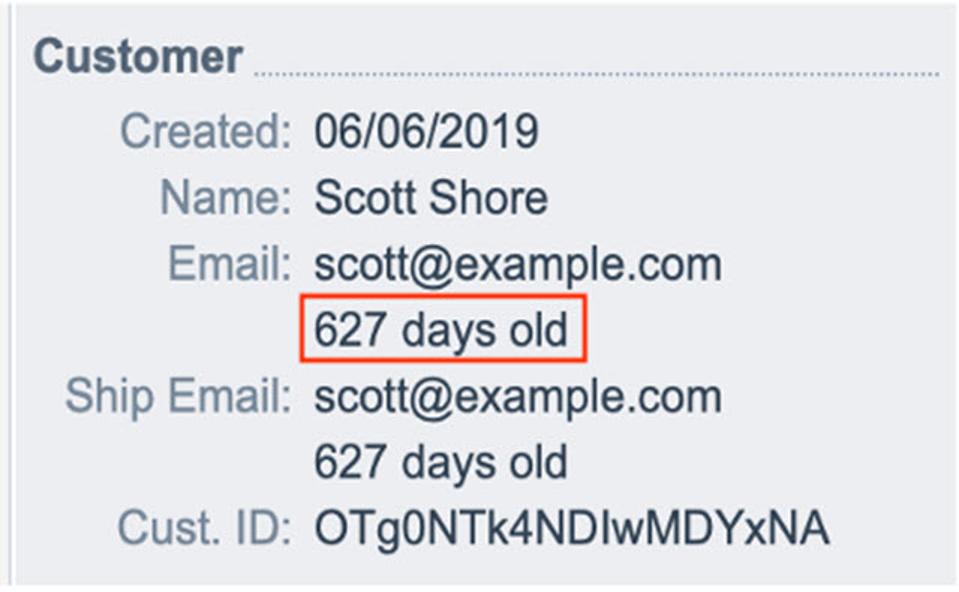
HTTPS://WWW.KOUNT.COM/
Kount’s Identity Trust Global Network relies on AI-based algorythms that can analyze all available identifiers or data points to establish real-time links between identity elements, and return identity trust decisions in real-time. Kount’s unique approach to using AI to improve customer experiences by reducing friction while blocking fraud reflects the future of fraud detection. In addition, Kount’s AI can discern if additional authentication is needed to verify the identity behind the transaction and relies on half a billion email addresses that are integral to AI-based analysis and risk scoring algorithms. Kount is making Email First Seen available to all existing customers for no charge. It’s been designed to be native on the Kount platform, allowing the information to be accessible in real-time to inform fraud and trust decisions.
Conclusion
In 2020 phishing attempts will increasingly rely on legitimate code, links, and executables as Trojan Horses to evade detection and launch phishing attacks at specific targets. Microsoft’s research and continued monitoring of phishing attempts uncovered architecturally sophisticated approaches to misdirecting victims through impersonation and social engineering.

Qatar

Commercial bank tower, West Bay,
15th floor, Doha, Qatar
PO Box 27111
+ 974 50 239 329
QATAR@CREAPIX.NET